The world of cybersecurity is fast-moving, and professionals who want to stay ahead need more than theory—they need hands-on practice. Setting up a Home Lab for Cybersecurity allows you to simulate real-world attack and defense scenarios, experiment with network configurations, and sharpen your firewall management skills without risking production environments.
In this guide, we’ll walk you through why you should build your own cybersecurity home lab, the essential hardware and software you’ll need, detailed setup steps, and the common mistakes you should avoid. By the end, you’ll know how to design a safe, scalable, and effective training environment from the comfort of your home.
Why You Need a Home Lab
If you’re aiming for a career in cybersecurity, building a Home Lab for Cybersecurity is not just a hobby—it’s a strategic investment. Here’s why:
- Safe Environment to Experiment: Break, fix, and rebuild without risking company systems.
- Hands-On Skills for Interviews: Employers value candidates who can demonstrate practical knowledge.
- Simulating Attacks and Defenses: Practice configuring firewalls, monitoring network traffic, and responding to incidents.
- SOC Environment Simulation: With the right tools, you can replicate the workflow of a Security Operations Center.
- Continuous Learning: Technologies change rapidly. A home lab lets you stay updated on new tools and attack methods.
Whether you’re preparing for certifications like CEH, CompTIA Security+, or CISSP, or just looking to master network defense, a Home Lab for Cybersecurity gives you the competitive edge.
Hardware and Software Requirements for a Home Lab for Cybersecurity

One misconception is that you need enterprise-level hardware. In reality, your Home Lab for Cybersecurity can start small and grow as you advance.
Hardware Requirements:
- PC/Laptop with Strong CPU (Intel i5/i7 or AMD Ryzen) – Essential for virtualization.
- 16–32GB RAM – More memory means more virtual machines running simultaneously.
- SSD Storage (500GB–1TB) – Faster load times and better performance.
- Network Switch or Router – Optional, but useful for practicing segmentation.
Software Requirements
When building a Home Lab for Cybersecurity, software is the real backbone. These tools let you create, monitor, defend, and attack networks in a controlled environment. Below is a breakdown of the most important categories and how each software contributes to your training:
Virtualization Platforms
- VMware Workstation Pro / Player – A professional-grade hypervisor that allows you to run multiple operating systems simultaneously. It is known for stability and enterprise-like features. While VMware Pro is paid, VMware Player is free and enough for beginners. Ideal for running multiple servers, firewalls, and client machines in your Home Lab for Cybersecurity.
- VirtualBox – A free and open-source virtualization solution from Oracle. Easy to install, widely supported, and perfect for learners. It may lack some advanced features compared to VMware, but it’s a cost-effective starting point.
- Proxmox VE – An open-source enterprise virtualization platform. Unlike VMware or VirtualBox, it runs directly on bare-metal hardware, giving you better performance and cluster management options. Perfect for advanced learners who want to mimic a corporate datacenter at home.
Firewall and Security Gateways
- pfSense – A free, open-source firewall and router platform based on FreeBSD. It’s extremely powerful and widely used in real-world networks. With pfSense in your lab, you can configure firewall rules, VPNs, intrusion detection systems, and traffic shaping. It’s the go-to choice for practicing firewall management.
- OPNsense – A fork of pfSense with a modern UI and additional plugins. It serves the same purpose as pfSense but may be easier to manage for beginners. Both are excellent for learning network defense.
Network Analysis and Monitoring Tools
- Wireshark – The most popular packet capture and analysis tool. With Wireshark, you can inspect network traffic in real time, identify suspicious packets, and understand how protocols like TCP/IP, DNS, and HTTP actually work. This is a must-have tool in any Home Lab for Cybersecurity.
- Nmap – A network scanning tool that allows you to discover devices, open ports, and running services on your virtual network. It’s essential for learning reconnaissance, one of the first steps in penetration testing.
- Metasploit Framework – A penetration testing platform that allows you to simulate real-world attacks, exploit vulnerabilities, and test defense mechanisms. Running Metasploit inside your home lab helps you understand how attackers operate—and how to stop them.
Network Simulation Tools
- Cisco Packet Tracer – A simulation tool created by Cisco that lets you design and visualize networks without real hardware. You can configure routers, switches, and firewalls in a safe virtual space. It’s perfect for students preparing for Cisco certifications or anyone practicing network fundamentals.
- GNS3 (Graphical Network Simulator 3) – A more advanced alternative to Packet Tracer. It allows you to run actual Cisco IOS images or other vendor network software, giving you a realistic simulation of enterprise-grade networks. Great for advanced learners aiming for professional networking roles.
Operating Systems for Testing
- Windows Server – Useful for learning Active Directory, DNS, DHCP, and enterprise management. You can practice user authentication, group policies, and security hardening.
- Linux Distributions –
Ubuntu: Beginner-friendly, widely used for servers.
Kali Linux: Tailored for penetration testing with pre-installed security tools. CentOS / Rocky Linux: Enterprise-grade, good for simulating corporate server environments.
By combining these software tools, your Home Lab for Cybersecurity transforms into a miniature enterprise network where you can simulate attacks, deploy defenses, and experiment with different architectures safely.
Home Lab Setup Steps
Setting up your Home Lab for Cybersecurity involves designing a network environment, choosing virtualization software, and layering security tools.
Virtualization (VMware, VirtualBox, Proxmox)
The foundation of your home lab is virtualization. Virtualization allows you to create multiple isolated operating systems on a single physical machine.
- VMware Workstation Pro: Industry standard, robust but paid.
- VirtualBox: Free and beginner-friendly.
- Proxmox: Open-source with enterprise-grade features.
Use virtualization to create different environments: a Windows workstation, a Linux server, and a pfSense firewall. Each can be configured to communicate with each other, just like in a corporate network.
Network Topology and Segmentation
Designing a small but realistic network topology is the heart of your Home Lab for Cybersecurity.
- LAN Segment: Internal network for testing.
- DMZ (Demilitarized Zone): Place a public-facing server (like a web server).
- Firewall: pfSense between LAN and WAN to control traffic.
- Monitoring Node: A VM running Wireshark or Security Onion for packet analysis.
By simulating segments and traffic flow, you’ll learn how to detect malicious packets, configure firewall rules, and prevent lateral movement of threats.
Tools to Practice: Wireshark, pfSense, Cisco Packet Tracer
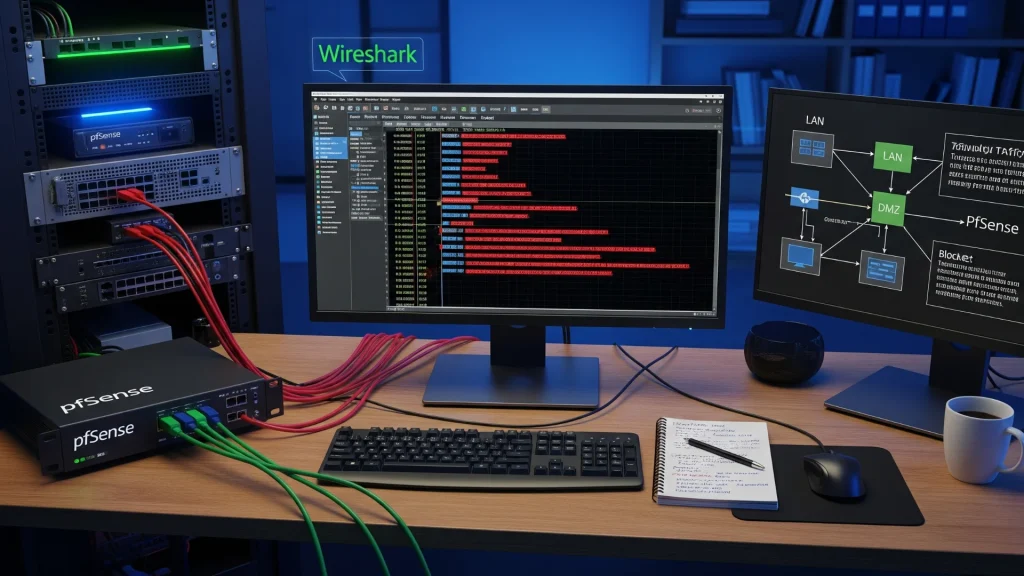
Once your basic lab is up, start experimenting with tools that security professionals use daily.
- Wireshark: Analyze packets in detail. You’ll learn to identify suspicious behavior such as port scanning or malware communication.
- pfSense: A powerful, open-source firewall you can install on a VM or dedicated device. Configure NAT, VPN, intrusion prevention, and filtering rules.
- Cisco Packet Tracer: Great for practicing routing, switching, and basic networking concepts in a safe environment.
Other advanced tools for your Home Lab for Cybersecurity:
- Metasploit for penetration testing.
- Security Onion for intrusion detection.
- Splunk or ELK Stack for SIEM practice.
These tools help you move beyond theory and gain practical skills for real-world scenarios.
Common Mistakes to Avoid
When building a Home Lab for Cybersecurity, beginners often make mistakes that limit their learning. Here are pitfalls to watch out for:
- Overcomplicating Too Soon: Start simple with one firewall and two VMs. Expand later.
- Ignoring Documentation: Keep notes of configurations and errors for troubleshooting.
- Not Isolating the Lab: Don’t connect vulnerable VMs directly to your home network. Use NAT or internal-only adapters.
- Skipping Backups: Take snapshots of your virtual machines. A clean restore saves hours of work.
- Lack of Clear Goals: Define objectives—whether it’s practicing SOC workflows, studying for a certification, or testing malware.
Avoiding these mistakes ensures your Home Lab for Cybersecurity remains a productive and safe learning environment.
FAQ
What is the best software for a Home Lab for Cybersecurity?
The best software depends on your goals. For firewalls, pfSense is excellent. For network simulations, Cisco Packet Tracer or GNS3 work well. For general monitoring, Wireshark is essential.
Do I need expensive hardware?
No. You can build a Home Lab for Cybersecurity with a mid-range PC or laptop. VirtualBox is free, and Linux distributions are open-source. Start small and scale as you advance.
How can I simulate a SOC environment at home?
You can deploy Security Onion, ELK Stack, or Splunk in your lab to collect logs, monitor traffic, and practice incident response just like in a professional SOC.
Take the Next Step with Bilişim Academy
Setting up a Home Lab for Cybersecurity is the first step toward becoming a skilled professional. But self-study alone can only take you so far. To accelerate your learning, consider structured training.
At Bilişim Academy, our Cyber Security Courses are designed to guide you from beginner to advanced levels with hands-on labs, real-world scenarios, and expert mentorship. Whether you’re preparing for certifications or aiming for a career in cybersecurity, our courses will help you master the skills you need.
Start your cybersecurity journey today with Bilişim Academy and turn your home lab into a pathway to a professional career.
In collaboration with our trusted SEO and Media Planning partner, we are proud to deliver cybersecurity education supported by strategic digital expertise.




